This tutorial provides a general introduction to VLAN's, and includes refreshers on IP addresses, subnetting, and switching.
It covers only static VLANs, although understanding these concepts is also necessary for understanding dynamic VLANs.
Computer networking is complicated. In order to manage that complexity, it's built in layers. One way of describing those layers is the OSI model, which breaks down all networking into seven layers.
For this tutorial, we're interested in the first three layers.
Layer 1 is the physical layer. This includes our physical network cables, the ports on our switches, the link lights on our switch ports, etc.
Layer 2 is the data link layer. This layer includes MAC (Media Access Control). Each network interface, whether it's in a printer or computer or switch, has a MAC address. MAC addresses look like C4:E9:84:00:5B:1B. Hardware manufacturers assign a unique MAC address for every network interface.
Layer 3 is the network layer. This layer includes IP (Internet Protocol) and IP addresses like 172.16.10.200.
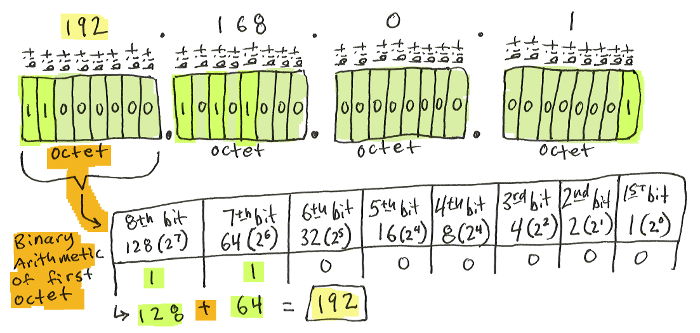
We often talk about IP addresses in dotted decimal format, like 192.168.0.1, but computers actually see them as binary numbers. This is important to understand because it's the basis of subnetting.
We call the "192" and "168" and "0" and "1" parts of the IP address "octets", because each of these decimal numbers corresponds to eight binary bits. In binary, 192.168.0.1 looks like:
11000000.10101000.00000000.00000001

(Search for binary arithmetic octet if you're curious.)
Keep in mind that IP addressing happens in network layer 3.
Subnetting is a way of dividing a network into smaller networks.
Computers on the same subnet can talk directly to each other. Traffic between computers of different subnets must be routed by a gateway.
How does Computer A know if Computer B is on its subnet or a different subnet? Computer A looks at its IP address and subnet mask to see if the masked address of Computer B matches its own network. If the network portions of the IP addresses match, Computer A finds Computer B using ARP (see below). If the network portion of the IP addresses don't match, Computer A knows Computer B is on a different network, and that it should send communications for Computer B to its gateway.
In the illustration below, Computer A knows that its subnet mask is /16, which means the first sixteen bits of the IP address are the network part (and the last sixteen are the host part). If the address of Computer B is 192.168.something.something, it's on the same network as Computer A.
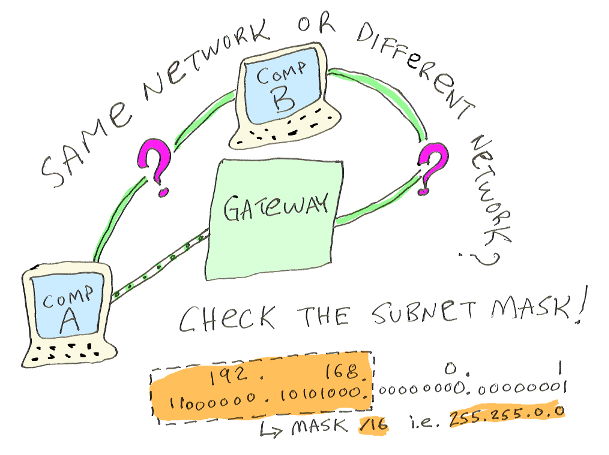
(The /16 style description for subnets is called CIDR notation. The 255.255.0.0 style is called dot-decimal notation.)
Keep in mind that subnetting, like IP addressing, is part of network layer 3.
If Computer A determines that Computer B is on its own network, how does it proceed with sending data? IP addresses and subnets are network layer 3 concepts. To send data, Computer A needs to drill down to layer 2 before it commences communication.
ARP is Address Resolution Protocol. This is where the IP addressing of network layer 3 meets the MAC addressing of network layer 2.
Each computer maintains an ARP table that maps layer 3 IP addresses to layer 2 MAC addresses.
If Computer A already knows the MAC address of Computer B from its ARP table, it can immediately send data to Computer B's MAC address. If Computer A does not already know the MAC address of Computer B, it must discover the MAC address by sending an ARP broadcast. It sends a packet addressed to its whole network, asking for the machine with the IP address in question (Computer B) to reply with its MAC address. When Computer A receives the reply, it adds Computer B's MAC address to its ARP table for later use.
Keep in mind that ARP happens in network layer 2.
First, not all network traffic uses Internet Protocol.
Second, consider a scenario where a server has two network cards (each with their own layer 2 MAC addresses) bound to the same layer 3 IP address. Alternately, consider the inverse—one network card with multiple IP addresses, perhaps even addresses on different networks.
Having both MAC addresses and IP addresses provides tremendous flexibility. It make VLAN's possible, for example.
First, let's review the difference between a hub and a switch.
A hub operates purely on network layer 1, the physical layer. It knows nothing about MAC addresses or IP addresses. Any traffic that comes in one port of the hub gets sent to every other port on the hub.
Not so with a switch.
A switch is aware of network layer 2, the data link layer. Just as each computer maintains its own ARP table, each switch also maintains an ARP-like table. However, instead of mapping IP addresses to MAC addresses, a switch's table maps switch ports to MAC addresses. This is called the CAM (Content Addressable Memory) table. A switch knows what devices are attached to it. Instead of sending data to all ports, like a hub, a switch sends data only to the port with a matching MAC address.†
† ...for unicast traffic. Most network traffic can be classified as unicast or broadcast. With unicast traffic, one host sends data to one other host. With broadcast traffic, one host sends traffic to all hosts on its broadcast domain; on IP networks, the broadcast domain corresponds to the sender's subnet. Broadcast traffic includes ARP and DHCP. Broadcast traffic can amount to a substantial volume of bandwidth; one of the advantages of vlans is that they limit broadcast domains.
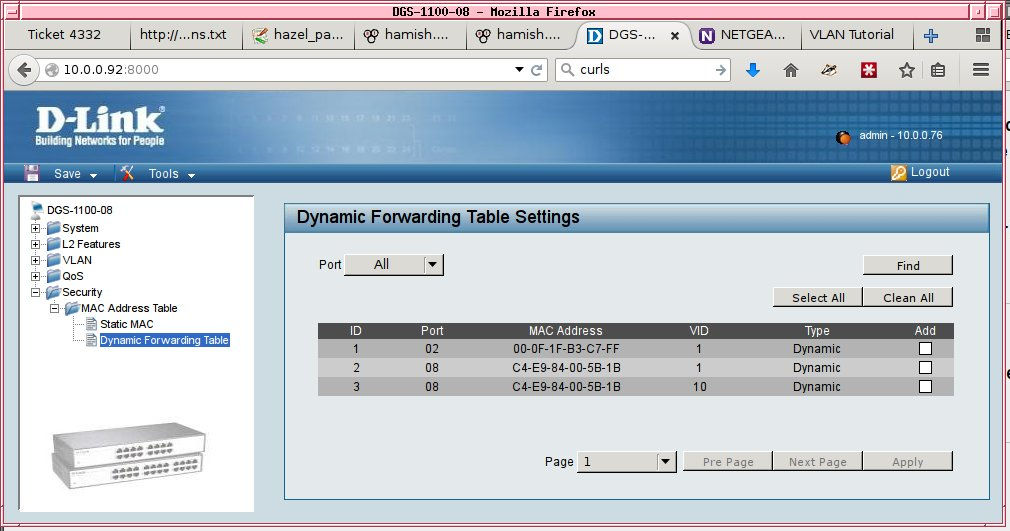
In the screenshot below, we see the web interface of a managed switch showing the CAM table that maps physical switch ports to the MAC addresses of connected devices:
Vendors sometimes used the terms "unmanaged" and "managed" in their marketing material for switches. Unmanaged switches are relatively "dumb", and operate as described above, transmitting packets according to a basic awareness of layer 2 protocols. Managed switches are relatively "smart". They offer some configuration options (usually over telnet, ssh, a console port, or a web-based interface), and may have some awareness of layer 3 protocols.
Most managed switches support VLAN's. Unmanaged switched are not aware of VLAN's. VLAN-encapsulated packets may or may not pass unmolested through unmanaged switches; it depends on the switch model.
Virtual Local Area Networks are simply a way of grouping devices on into broadcast domains (subnets) logically, rather than having the broadcast domain dictated by the physical network.
VLANs offer a number of benefits, including increased security of LAN traffic, better traffic management/quality of service, and network abstraction that lets us do things like grouping computers on different physical network segments into the same logical network.
VLAN's work by "tagging" packets with a VID (VLAN Identifier). This is properly called "802.1Q encapsulation". It inserts 32 bits (which includes the VID) into the packet's ethernet frame, which are read by VLAN-aware devices.
We configure each port on a VLAN-aware switch as a member of a particular VLAN.
Whereas a non-VLAN-aware switch keeps a simple CAM table mapping switch ports to MAC addresses, a VLAN-aware switch also keeps track of which ports belong to which VLAN's. To send data to a switch port, not only must the MAC address of the attached device match the packet headers, but the port must also be a member of the VLAN specified by the packet's VID.
On an unconfigured switch, all the ports are members of the default VLAN (typically VLAN 1).
If we create a new VLAN—VLAN 2, for example—and make switch ports 1-4 members of the new VLAN, then any devices plugged into ports 1-4 can send packets to each other. Devices on any other ports, which are still part of default VLAN 1, can no longer communicate with devices on the new VLAN.
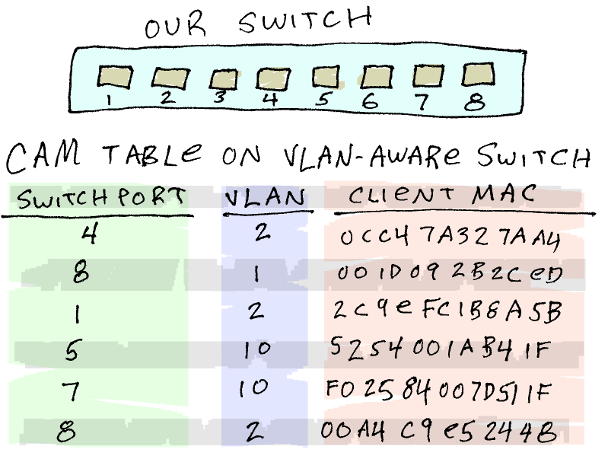
Traffic between VLANs must be directed by a layer 3 device like a router, because the VLANs are effectively different networks.
The devices on VLAN 2 (ports 1-4) might be part of subnet 192.168.100.0/24, while devices on VLAN 1 belong to the 10.0.100.0/16 network. Because the CAM table of our switch knows the VLAN membership of each port, even broadcast traffic (like ARP requests) from VLAN 1 will not be sent to ports belonging to other VLANs. This reduces network congestion and improves security.
Think about the flow of packets through the switch in terms of ingress and egress.
A packet must enter the switch (ingress) through one of its physical ports. That packet may already be encapsulated with a VLAN tag/VID, or it may not. Most user workstations don't understand VLANs, so packets entering the switch from a port connected to a workstation will probably not have an existing VID.
What does the switch do with an untagged packet when it enters the switch? The switch tags/encapsulates the packet with the PVID (Port VLAN Identifier) configured for that physical port.
What happens if the packet is already tagged/encapsulated before it enters the switch? The switch leaves the existing VID in place on the packet. (This might happen if the device attached to the port is another switch, a router, or a VLAN-aware server.)
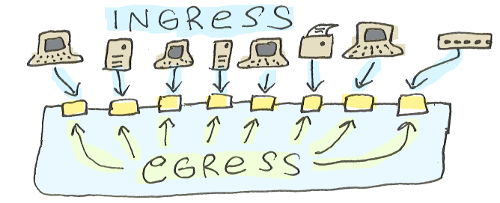
Once a packet is inside the switch, it's time to think about egress.
If the packet is a broadcast packet, the switch sends it out every port that is a member (i.e. an "untagged" or "tagged" port for that VLAN) of the VLAN matching the packet's VID. If it's a unicast packet, and destination address happens to be attached to a port that belongs to the VLAN matching the packet's VID, the switch sends the packet out the correct port. If the destination address of the packet is for a machine attached to a port that's not a member of the VLAN specified in the packet's VID, the packet gets dropped without reaching its destination.
What's this business with "tagged" and "untagged" for egress?
A switch port that's a tagged member of a VLAN sends packets out of the switch with their VLAN encapsulation intact. The switch expects that whatever device is attached to that port needs to know the VLAN information and is capable of handling it. Typically, the device on the other end is another switch or a router. Uplink ports between switches are often tagged for multiple VLANs.
A switch port that's an untagged member of a VLAN strips the VLAN encapsulation from packets before sending the packets out of the switch. This happens because whatever device is attached to that switch port can't handle or doesn't need to know about the VLAN information. Such devices include most user workstations, printers, kiosks, VOIP phones, etc. The majority of ports on most switches will be untagged members of one VLAN.
The methods and specifics of configuring switches vary between manufacturers and product lines.
Most switches offer web-based configuration, and many also offer command-line configuration (telnet, ssh, serial console). Consult the manual for your switch.
Regardless of the specific tool used, initial configuration involves the following steps.
The screenshot below, from the web-based configuration page of a popular manufacturer, shows that we've created three VLANs in addition to default VLAN 1. Ports 1-2 are members (untagged) of VLAN 1, ports 3-6 are members of VLAN 20, and port 7 is a member of VLAN 30. Port 8, used as the uplink to our router or another switch, will send out traffic (tagged) for all the VLANs.
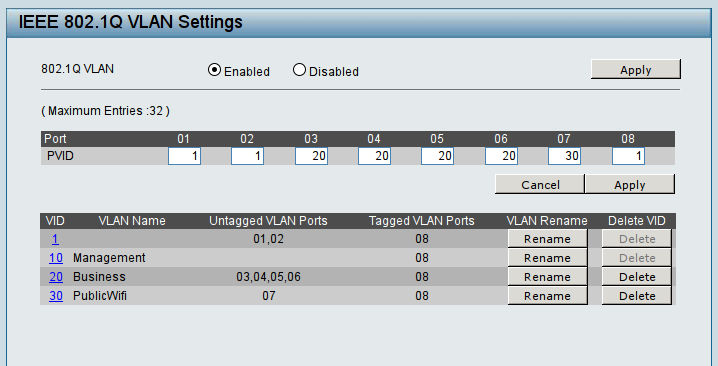
Note that that our uplink port, port 8, has the PVID 1. We expect that most traffic coming from another switch will already have a VID, but if it does not we dump it into the default VLAN by encapsulating it with VID 1.
Most switches allow us to specify a management VLAN, which we use to connect to the switch's IP address when managing the switch itself. This is a security feature, to prevent users on non-management VLANs from connecting to the switch.
On an unconfigured switch, the management VLAN is probably the same as the default VLAN. Create a dedicated management VLAN that is not the default VLAN.
In order to not lock administrators out of the switch, we must do one of two things. The first option is to dedicate one physical port on the switch as a management port, as a member of the management VLAN with a PVID matching the management VLAN. However, it may not be convenient to physically plug a management laptop into the switch every time we need to access it. The other option is make our uplink port tagged for the management VLAN. This is more convenient, because we can (with care!) safely expose the management VLAN to administrator workstations using access controls on our layer 3 device (e.g. router or firewall).
In any case, make sure to set the PVID of uplink ports as the default VLAN, not the management VLAN!
A lot of VLAN documentation found on the web uses Cisco terminology, which differs from that used by most other manufacturers.
Host B (given Host B's IP address) is directly reachable on its own network?Host A send traffic for Host B if Host B is not on the same network?© Paul Gorman 2015